Secure your environment from inside out
You can't protect a house with no windows against robbery, so always start building your resilience by establishing and challenging your outer gates. Once you have built and challenged your outer gates, develop your resilience from the inside out. An attacker will eventually get into your network, and any organization should be capable of detecting and stopping an attack even if the attacker is already inside. We believe the key to resilience is knowing what and where your core assets are and how to protect them.
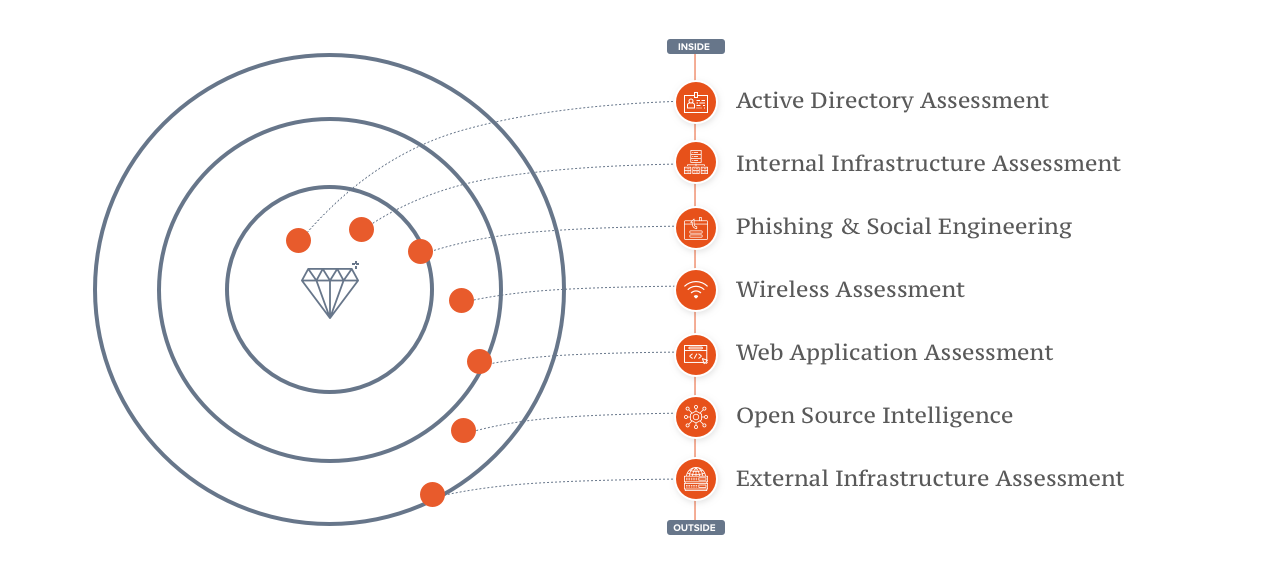
Our services
We offer services to identify and mitigate vulnerabilities in all areas of your organization, covering all steps a real attacker would need to take. Find a list of some of our core services below. Get in touch with us to explore how these can help you test your flagship applications, a specific attack scenario, or simulate a realistic attack.
Penetration Testing
- Web Application
- Mobile Applications
- Infrastructure
Scenario-based Assessment
- Stolen Device
- Malicious Insider
- Infrastructure
Red Teaming
- TIBER EU
- TLPT
- Purple Teaming
Access Assessment
- Phishing Assessment
- Social Engineering
- Wireless Assessment
- OSINT Assessment
Environment Review
- Active Directory Review
- Infrastructure Review
- Network Review
Awareness & Trainings
- Awareness Talks
- Workshops
- Purple Teaming
Tailored Services
- ICS / OT / SCADA Assessment
- IoT Assessment
- Hardware Assessment
Strategy Consulting
- Attack Surface Mapping
- GAP Analysis
Contact for Offensive Security




