
Insecure defaults often lead to vulnerable implementations. This blog post explores such an insecure default in the Node.js crypto module, which breaks authenticity and affects many implementations in practice.

Teetje Stark
18. April 2024

Embedding Scalable Vector Graphics (SVG) can expose websites to code injection. This article explores how SVGs work, the risks they pose, and how to mitigate them.

Teetje Stark
24. Juli 2023

This spotlight covers the Microsoft Configuration Manager (ConfigMgr), also known as SCCM or MECM.
Get an intro into the Configuration Manger, an overview and demonstration of known attacks against it, practical tool box knowledge and best practice defensive guidelines.

Carsten Sandker
17. Mai 2023

In this blog post an overview of the different components of a red team infrastructure is given. This includes explanations how these work, as well as the comparison of different solutions and their characteristics.

André Tschapeller
27. April 2023
User enumeration in Azure Active Directory environments is an important step in attack simulations. This blog post revisits how user enumeration can be performed for Microsoft Teams and introduces a new tool called TeamsEnum.

Bastian Kanbach
4. April 2023

This blog post evaluates the state of the art with phishing, which techniques are still relevant and what know-how is worth revisiting. Additionally an overview of various techniques across the three stages of a phishing campaign, an overview of features supported by different Microsoft Office applications and a VirusTotal benchmark are included in this post.

Carsten Sandker
9. Februar 2023

DNSSEC uses resource records like NSEC or NSEC3, which can be leveraged for subdomain enumeration. Different techniques for zone enumeration and countermeasures like White Lies and Black Lies are described in this blog post.

Bastian Kanbach
29. November 2022

One of the most relevant techniques during the reconnaissance phase of an engagement is Subdomain Enumeration. This post aims to enhance subdomain enumeration by including a special DNS node (ENT) and the NOERROR response code that is often ignored.

Bastian Kanbach
10. August 2022
Windows Event Forwarding (WEF) offers a simple, free and already built-in solution to configure Windows workstations and servers to send encrypted log events to a centralized location for storage, analysis, attack & anomaly detection...

Carsten Sandker
22. Juli 2022

In this blog post, we would like to raise awareness for an often underestimated problem: the lack of publicly available information about the security specifications of modern Android smartphones on the market.

Tim Ohlendorf
14. Juni 2022
During an engagement in early 2021 my colleague and myself stumbled across an FTP server with a banner that we've never seen before...

Carsten Sandker
5. Mai 2022
Connaisseur is a Kubernetes admission controller for container image signature verification. The latest release v2.2 improves usability...

Dr. Christoph Hamsen
18. Oktober 2021
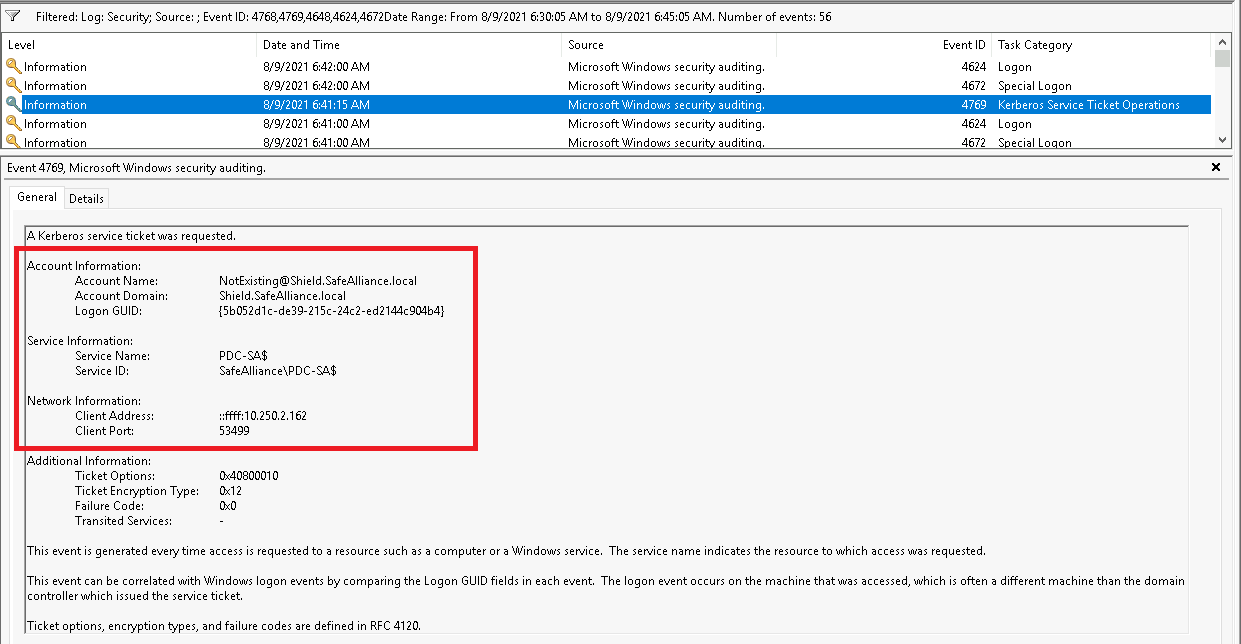
This is part 2 of our Active Directory Trusts series. This part will cover guidance for red and blue teams on how to enumerate, attack and secure AD trusts.

Carsten Sandker
10. Oktober 2021
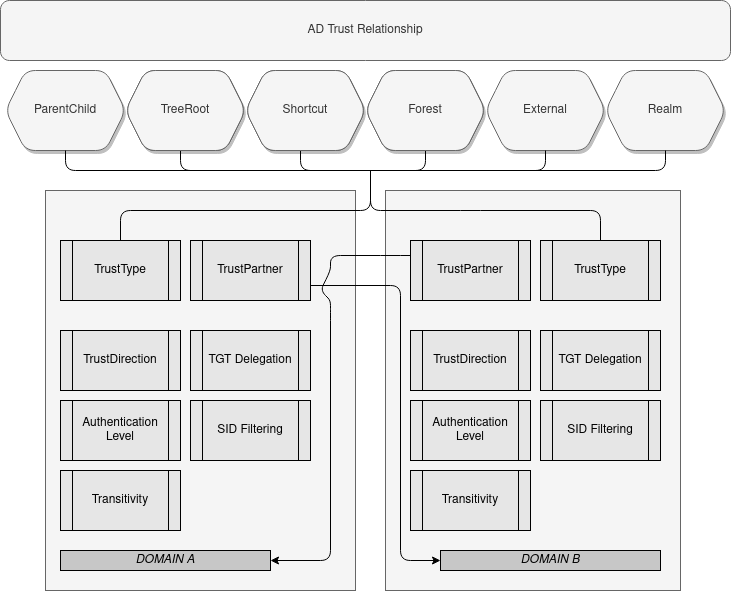
This post is intended to shed some light on Active Directory Trusts, to understand, dissect, configure and find vulnerabilities in AD trust environments.

Carsten Sandker
10. Oktober 2021

Container image signatures are a rarely implemented security feature, even though images' contents are ever changing and hard to get a grasp of, making it easy for attackers to hide malicious content in them.

Dr. Christoph Hamsen
27. Juli 2021
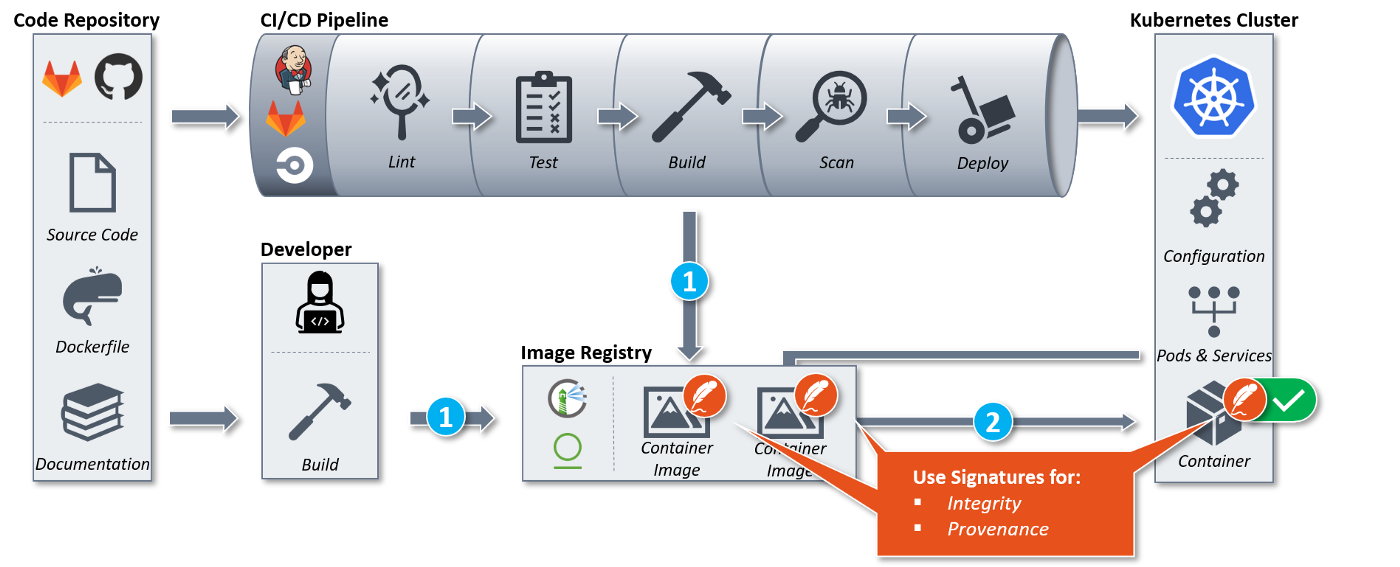
Connaisseur v2.0 adds support for multiple keys and signature solutions.

Dr. Christoph Hamsen
27. Juli 2021

Default AKS cluster stores admin credentials in Kubernetes ConfigMap.

Anneke Breust
17. Juli 2020

A central question in application security is: how do we ensure that our Docker containers actually run the code that we intend to run?

Dr. Peter Thomassen
14. Juli 2020

Tackling a New Challenge with the DNS

Dr. Peter Thomassen
12. Juli 2020

